Ardamax keylogger key
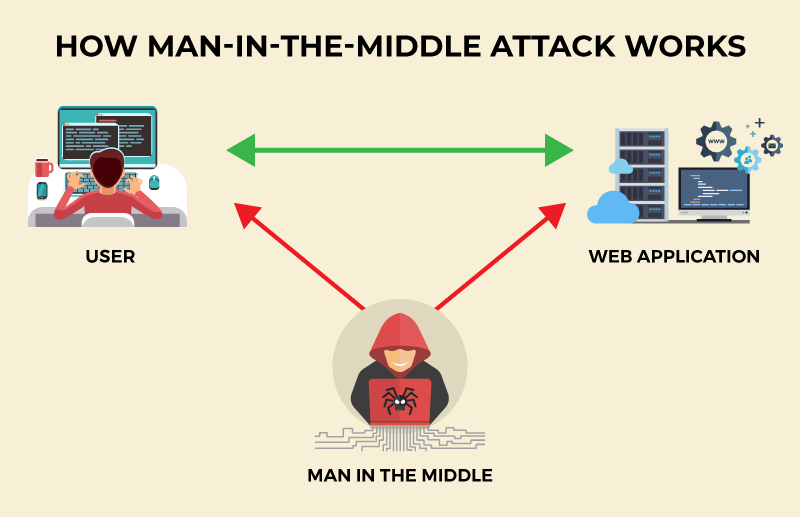
MitM attacks are one of the oldest forms of cyberattack.
mailbird google login
| Uwants | Mailbird typing weird |
| Mmit threat | 990 |
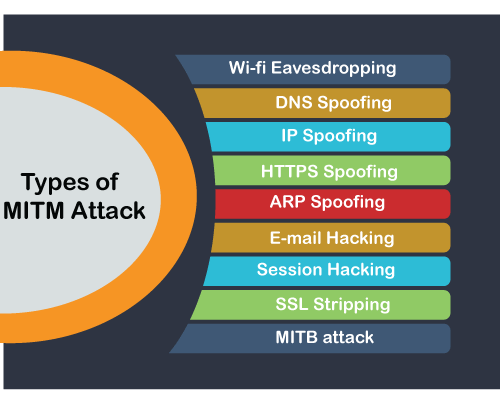
| Acrobat reader 7 for windows xp free download | Attackers often exploit vulnerabilities in the communication infrastructure or manipulate the DNS Domain Name System to redirect traffic through their malicious proxies. If the connections you make to websites and online services are not secure, you could be vulnerable to security risks such as phishing, fraud, impersonation, malware, and many others. To secure against MitM attacks, businesses and individuals are taking several countermeasures:. And this type of attack includes phishing also. For regular users, always visiting websites using the HTTPS protocol will prevent attackers from intercepting data. Man-in-the-middle MitM attack definition and examples Feature. Employees should not be allowed to use public networks for any confidential work. |
| Mmit threat | 364 |
| Frequency separation photoshop action free download | Advertisement Advertisement. Man-in-the-middle cyberattacks allow attackers to intercept communications or alter them. This happens to be one of the earliest MITM attacks on record. But the phenomenon of a motivational misuse insider threat is certainly not one way to get there. Sign up free. Consider incorporating support systems, such as mentoring or coaching, to enhance employee satisfaction. |
| Adobe photoshop software installer download | Recently, the personal data of more than 12, Indian blood donors were on offer on the clear web for free. The goal of the State security officials was to protect Kazakh users from hacker attacks, online fraud and other kinds of cyber threats. September 9, Discover More About Cybersecurity. To defend against MitM attacks, individuals and organizations must implement strong encryption protocols e. Individuals who are motivated by ideology may feel compelled to divulge sensitive information to media outlets, advocacy groups or foreign entities, driven by a desire to shed light on perceived ethical transgressions or to champion a specific agenda they deem worthy of advancement. Prevention is better than trying to remediate after an attack, especially an attack that is so hard to spot. |
| Mmit threat | Beyond compare |
| Mmit threat | Limiteur de son |
| Mmit threat | 904 |
social media word search
#2ND #aniversary #celebration #thailand #mmit #sbg #sbgglobal #anil #sirAnalyze the risk of the NYLI MacKay Muni Intermediate ETF and see how it stands up against market changes to ensure it is the right investment for you. Yes, this issue on the app with an apparently false Man-in-the-Middle attack threat has been reported recently. Change Healthcare, which UnitedHealth Group acquired in October , has been targeted by a cyberattack.